| Security Tips |
- Online shopping security
|
While purchasing online, look for signs that these are secure (SSL secured sites or 128 bit encryption) like shopping.rediff.com. At the point when you are providing your payment information, a golden-coloured lock appears (for SSL secured sites) on the right hand side corner of the browser or the beginning of the Web site address should change from http to https, indicating that the information is being encrypted ie turned into code that can only be read by the seller.
- Your browser may also signal that the information is secure with a symbol, such as a broken key that becomes whole or a padlock that closes.
- Carefully use credit-cards and online banking for online shopping. Check your credit card and bank statements at regular intervals. Notify the bank immediately if there are unauthorised charges or debits. Avoid using credit card details and online banking on public computers and in cyber cafes. It is very unsafe because most of them are infected with viruses, trojans and key loggers.
- Some banks have launched their services like Net Safe to create temporary credit cards with a limited value to transact online. Paypal is also a secure way to do the transactions .This way, in the worst case scenario you can minimise the impact.
|
Sunday, 30 September 2012
Online shopping security
What’s good password
- What’s good password ?
|
- Use different passwords for different Web sites. Maintain separate passwords for e-mail, work and other important Web sites and routine web- surfing.
- Use difficult-to-guess password by taking the first alphabet from each word of a phrase. What is a good password? It is a password which is at least 8 characters long, not easily guessable, contains mixture of uppercase and lowercase letters as well as numbers, and preferably contains special characters like $, *, %, !, * etc. Some examples of a good password are: &(^.3235*cRack&.^).
- Always use alphanumeric passwords with special characters and try to adopt phrasing technique to construct passwords which are easy to
remember, hard to guess and impossible to crack. Create a unique acronym. Never use a dictionary based password like guest, home etc. It takes little time for a good cracker to crack the password. |
How to protect computer from internet hackers
- How to protect your computer from internet hackers
|
You do it every day. Log into your computer, send e-mails, open attachments, shop online, transfer money using your bank's secure payment gateway, chat, and upload personal information on social networking and job Web sites. Here's a thought: what if someone was watching everything you were doing?
Just like someone who hacked into Ken Haywood's Wi-Fi connection was and sent threat mail just a few minutes before the first of many bombs went up in Ahmedababd. Given the lax security that users as well as internet service providers have cyber criminals are always on the watch out for vulnerable people whose computers could be at risks.
There's a worryingly large possibility that someone could be keeping a close watch on all your online activities. From any corner of the world, someone could get inside your computer every day, and could have access to one of the most important resources of the information age: Your Personal Data.
Personal Data can be abused to make online purchases, carry out attacks against all those on your contact list and an innumerable list of things that can harm your everyday life. Welcome to the age of hackers (these are people who try to gain access to your computer using various hacking tools and misuse your personal data) and spies lurking on the vast Internet highway.
If that got you worked up, breathe. There are many ways in which you can defend yourself against hackers -- even though when it comes to security, nothing can give you 100 per cent guarantee. A host of new tools and exploits are developed every single day, so updating the knowledgebase to counter them must be a regular process.
|
General computer security
General computer security
|
Install the latest Antivirus Software on all your computers and never disable them. Popular antivirus softwares include Kaspersky, Bit Defender, Nod32, Antivir, Grisoft AVG and Quickheal. Also install a personal firewall and an anti-spyware solution. Popular firewalls include Antivir, Grisoft AVG, Quickheal, 3Com and Sonicwall.
Update antivirus/ anti-spyware/ firewall at least every 15 days. Carry out a complete system scan with your anti-virus at least once a week, or better, auto-schedule it to run every Friday.
There are a few free online antivirus scanners available at Trend-Micro, Kaspersky and F-Secure.
Don't download or open attachments from unknown senders. Even if the sender is trusted, ensure that the content is relevant. Even non-executable files like *.doc files can contain macro viruses and Trojans. There are some dangerous programmes called worms, which don't need human interaction. You can be infected by simply opening an e-mail or by visiting a Web site and that's it. So always stay alert. Avoid opening e-mail attachments that contain .vbs, .scr, .exe, or .pif file extensions. Files that end in these extensions are most likely to contain some sort of viruses.
Latest Web browsers such as Firefox, IE 7 & Opera offer innovative new security features, so it is necessary to update old browsers to their latest versions.
Never download any files especially executable files over P2P sharing networks (peer-to-peer), as you can never be absolutely certain as to what they really are. P2P file sharing programmes can lead to the installation of a lot of adware and spyware. Try downloading executables from authentic and well-known Web sites; don't download files from any random Web site.
Try not to visit warez, porn sites or Web sites that provide cracks and serials because most of them have a lot of spyware, trojans and viruses. A single visit and you are most likely infected with hundreds of malicious programmes.
Be familiar with the programmes installed on your computer. If you notice that a new programme is installed without your permission, possibilities are that it might be something malicious.
Read the installation agreements carefully when you download something from the Internet. Pay attention to the terms and conditions or EULA (end-user license agreements) of the programme being installed. Reference to third party installation should be given more attention. Some EULA's tell you that, if you install the programme, you have to also agree to install some spyware with the software. Check the independent sources, because some EULA's do not mention about the spyware.
Back-up your computer on a regular basis, at least weekly. Copy your important documents and files onto a USB drive, CD or a DVD for safekeeping. Don't wait for the disaster to happen, take the precautions beforehand. Create system restore points periodically.
Never respond to unsolicited e-mail. To those who send spam, one response or 'hit' from thousands of e-mails is enough to justify the practice. Additionally, it validates your email address as active, which makes it more valuable, and therefore opens the door to more spam.
Beware of phishing attacks. Sites like AntiPhishing offer latest updates on phishing along with some good security tips.
Don't chat with strangers or accept any file, especially executables from an unknown person on chat. Don't click on any links given by someone you don't know.
Do not accept links or downloads from strangers even if it is tempting. There have been cases where spyware like trojans and key-loggers have been hidden in simple picture files with .jpg extensions. You never really know what is contained inside a file which looks attractive.
Be cautious while displaying your profile, especially your personal details, photographs, videos and contacts on social networking sites. Your profiles and contacts may be misused by other people.
Install parental-control or filtering softwares like those from Websense (LINK) that helps you choose what can be seen on the Internet and monitor the activities of any users
|
INTERNET SECURITY TIPS
- Securing your wireless network
| ||
The whole aspect of security of wireless networks has become very important ever since terror e-mails were sent to media by alleged terrorists. Terrorists used unsecured wireless networks to hack into an individual's Wi-Fi network and sent e-mails just before bombs went off in Ahmedabad and New Delhi.
It is in this environment protecting your unsecured Wi-Fi network becomes very important lest somebody misuses the same.
Here are 10 simple ways in which you can secure your wireless network :
| ||
1. Change default administrator usernames and passwords :
Most routers or access points come enabled with a default set of username / password combinations. These combinations are well documented and available online for hackers to use. If a hacker can access your device's administrative pages they can modify the configuration and control all aspects of your device. These username / password combinations can be changed from the administrative panel and should be set to something difficult to guess. Keep a password which is difficult to guess and not easy to crack. A good password is 8 characters long, not easily guessable, contains mixture of uppercase and lowercase letters as well as numbers and preferably contains special characters like $,*,%,!. | ||
2. Turn on encryption :
All wireless devices support some form of encryption. Encryption technology scrambles messages sent over the air and ensures that they cannot be intercepted by hackers. Several encryption technologies exist for wireless communication today. WPA is the strongest commonly available encryption technology for home devices. While WEP can also be used cracking WEP is just a matter of few minutes. We would advice corporates to go for WPA with EAP Authentication, TKIP / RC4 Encryption or WPA 2 with EAP Authentication, AES-CCMP encryption for better security. | ||
3. Change the default SSID :
Access points and routers all use a network name called the SSID. Manufacturers normally ship their products with the same SSID set for all routers. For example, the SSID for Netgear devices is normally 'NETGEAR'. The default SSID can be changed from the administrative panel and should be set to something unique. | ||
| 4. Enable MAC Address filtering : Each wireless device possesses a unique identifier called the physical address or MAC address. Access points and routers keep track of the MAC addresses for all devices that connect to them. Wireless routers offer the option to key in the MAC addresses of your home equipment so as to restrict the network to only allow connections from those devices. It ensures that rogue users cannot connect to the wireless router without using advanced MAC spoofing techniques. | ||
| 5. Disable SSID Broadcast : The wireless access point or router typically broadcasts the network name (SSID) over the air at regular intervals. This feature was designed for businesses and mobile hotspots where wireless clients may roam in and out of range. For the home user, this roaming feature is unnecessary, and it increases the likelihood someone will try to log in to your home network. Fortunately, most wireless access points allow the SSID Broadcast feature to be disabled by the network administrator. Your SSID name can be manually entered into your devices to prevent the need for SSID Broadcasts to be enabled. | ||
6. Do not auto-connect to open wireless networks :
Connecting to an open wireless network such as a free wireless hotspot or your neighbour's router exposes your computer to security risks and attacks. Although not normally enabled, most computers have a setting available allowing these connections to happen automatically without notifying the user. This setting should not be enabled except in temporary situations. | ||
| 7. Assign static IP addresses to devices : Most home wireless devices use dynamic IP addresses. DHCP technology is indeed easy to set up. Unfortunately, this convenience also works to the advantage of network attackers, who can easily obtain valid IP addresses from your network's DHCP pool. Turn off DHCP on the router or access point, set a fixed IP address range instead and then configure each connected device to match. Using a private IP address range (like 10.0.0.x) prevents computers from being reached directly from the Internet. | ||
| 8. Enable firewalls on each computer and router : Modern network routers contain built-in firewall capability, but the option also exists to disable them. Ensure that your router's firewall is turned on. For extra protection, consider installing and running personal firewall software on each computer connected to the router. | ||
| 9. Position the router or access point safely : Wireless signals normally reach to the exterior of a home. A small amount of signal leakage outdoors is not a problem, but the further this signal reaches, the easier it is for others to detect and exploit. Wireless signals often reach through neighboring houses and into streets. When installing a wireless home network, the position of the access point or router determines its reach. Try to position these devices near the centre of the home rather than near windows to minimise leakage. Many routers allow you to reduce the range of your router from the administrative panel to prevent the signal leakage. | ||
| 10. Turn off network during extended periods of non-use : The ultimate in wireless security measures, shutting down your network will most certainly prevent outside hackers from breaking in! While impractical to turn off and on the devices frequently, at least consider doing so during travel or extended periods of downtime. |
Your Facebook Account Hacked? Protect it Now!
Facebook has become a popular platform not only for social networking but also for business promotion. You will find many brand exposure on Facebook these days. But how will you feel when such an important account gets hacked? In the present scenario, hacking a Facebook account is quite alike hacking the email account or the bank account. It’s true that your life seems to get ruined when your Facebook account gets hacked.
Many users spend hours after hours staying online on these sites and hence, such a breach of act can affect them adversely. When your account gets hacked, all your personal details are hijacked and spam mails are sent to a number of high grade professionals. Want to safeguard yourself from getting hacked?
Follow these steps and protect yourself.
Turn the Login Notifications on
Turning on the login notifications will warn you whenever the Facebook account is accessed from some other device. How to enable this notification?
Go to Account Settings > click on Security icon > choose Notifications > put checkmark beside the box labeled as ‘Browse Facebook on a secure connection (https) when possible’ > click on Save Changes. You are done! By enabling this, you will at once get a mail, if someone else tries to access your Facebook account.
Enable Secure Browsing
Secure Browsing makes use of encrypted connection in place of standard one. This protects your Facebook account by scrambling your data in order to prohibit the third party user from stealing your
Facebook details through some other network. Don’t you have turned on Security Browsing? Go ahead now.
Step 1: Go to Account Settings
Step 2: Click on Security icon
Step 3: Choose Secure Browsing * Edit
Step 4: Check the box beside ‘Browse Facebook on a secure connection (https) when possible’
Step 5: click on Save Changes
Isn’t this an easy process? Try it and enable the security feature.
Beware of Scams
Nowadays, you must have seen ‘Remove Facebook Timeline’ scam quite often in your account. Don’t make the mistake of clicking on ‘Like’ or ‘Continue’ since this may enable the scammer in hacking your\ account. Whenever you find some alarming message in the status update of your Facebook, Google it and verify it before proceeding further with it.
Change the Password Often
Most of the users do not have the habit of changing the password quite often. If you find some weird message that you have not posted on the wall of your Facebook account, you should be confirm that your account is hacked. The first measure that you need to take in this regard is changing of the password as soon as possible.
A password should always be a combination of characters, numbers and letters so that hackers have problem in guessing your password. Hacking your email account means getting access to all your recovery mails as well. Hence secure your mail account.
When you are browsing the web world, make sure that you have sufficient security software and protection. Enjoy safe online access!
AVIRA ANTIVIRUS PREMIUM 2012 12.0.0.865 | FINAL CRACK + SERIAL KEYS
AVIRA ANTIVIRUS PREMIUM 2012 12.0.0.865 | FINAL CRACK + SERIAL KEYS
DOWNLOAD

Avira Antivir 2012 http://premium.avira-update.com/antivir.exe
Serial Keys http://rapidshare.com/files/2339055374/Keys.rar
Note that the serial keys last till 21/01/2012 , dont worry much, they'll be updated, and make sure to turn off your internet connection before using any of the keys or else it wont work
Free Antiviruses of 2012 with Download link
Best Free Antiviruses of 2012 with Download link
1.) NORTON ANTIVIRUS 2012 19.6.2.10 [Incl. ACTIVATION + UPDATE]
Click HERE to Download
Here are some key of Norton AntiVirus 2012:
Engineered for Speed: Scans only files and processes at risk using Norton Insight.
NEW! Installs in under one minute on average, requires less than 8 MB of memory
Up-to-the-minute Protection: Delivers up-to-the-minute protection with rapid pulse updates every 5 to 15 minutes.
IMPROVED! Provides multilayered security through the Norton Protection System. Prevents bots from taking control of your PC.
Detects and automatically removes malicious threats.
IMPROVED! Defends against Web-based attacks.
Engineered for Speed: Scans only files and processes at risk using Norton Insight.
NEW! Installs in under one minute on average, requires less than 8 MB of memory
Up-to-the-minute Protection: Delivers up-to-the-minute protection with rapid pulse updates every 5 to 15 minutes.
IMPROVED! Provides multilayered security through the Norton Protection System. Prevents bots from taking control of your PC.
Detects and automatically removes malicious threats.
IMPROVED! Defends against Web-based attacks.
Click HERE to Download
========================================================================
2.) AVG Internet Security 2012 Final& FULL + Working Serials
Monday, 24 September 2012
Adfoc.us bot v 1.5.2 Bot Free download | Earn frequent cash
Adfoc.us bot v 1.5.2 Bot Free download | Earn frequent cash

Requirements:
- IE7+
- an adfoc.us account
Adfoc.us bot v 1.5.2 Bot Free download
Download Link :http://adfoc.us/209186777067
Fresh Proxy list : http://adfoc.us/209186804606
Virustotal Scan Report : http://adfoc.us/209186804632
>open rar file with given password
>extract and run
>goto setting and paste the fresh proxies
>paste ur Adfoc.us link into the column and press start

Saturday, 22 September 2012
Trick to change the admn password in win7 without knowing the current one...
1. Go to control panel and double click on administrative tools.

5. now double click on Users.
7.now Right click on Administrator you will see 1st option set password…. :D now just select that option.
How to crash small websites using RDOS
DOS TUTORIAL
How to crash small websites using RDOS
Have you ever wanted to DOS attack on a website. Here I am going to write about a tool which is really helpful but it wouldn't be effective on big servers.
NOTE: Please do not try to this tutorial to harm any other's website. I will not be responsible in any case. If you are not agree, please leave this website without reading further tutorial.
for cool computer tricks click here
You need:
- Port Scanner Download Here
- rDOS Download Here
- Ip Hiding tool Download Here
Follow these steps:
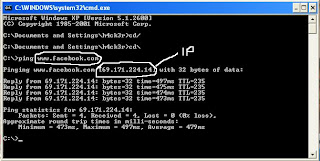
Use ping command in windows to get the ip address of the website.
open CMD and enter ping www.website.com
see the snap
Now you have the IP address of the website.
2: Now use Port scanner to check whether PORT 80 is open or not. If PORT 80 is not open choose another website to hack :P
otherwise you can crash this website.
3: Now open your rDos. Enter your victims ip that you got from step 1.
It will ask you for the port to attack use port 80 that’s why we scanned to make sure that 80 was open! If it is closed it will not work.
comment if you have any problem
DOS ATTACK ON WEBSITE
DOS (Denial Of Service) attack is one of the most powerful attack that is capable of crashing web servers. In this attack, attacker sends fake requests to server and floods its request queue with millions of Fake requests. In this way, server will not be able to handle valid request by a valid user. DOS attack becomes more popular when it is performed by millions of computer simultaneously on a single target. This is called Distributed Denial Of Server (DDOS) attack. DDOS attack is millions times more popular that DOS attack and its strength depends on the number of systems attending the attack.
There are many DOS attacking tools are available which can be found here.
Dos Attacking Tools
But LOIC (Low Orbit Ion Cannon) is the best tool for DDOS attack and it is also used by most popular hacker group annonymous. There are two versions of this tool. One is the original binary version of the tool and other is the web based version called JS LOIC.
The best thing about this tool is that the tool does not require any kind of technical knowledge. It is so simple iin use. Just specify the the website and click on the attack button.
Step 1: Run the tool. You will see the simple interface.
Step 2: At the top of the tool, there are two options. One for URL and other for IP. You can use any one. Enter the URL of the website which you want to take down. Now click on Lock On button. After that you are ready to attack on the website. Then, select attack method (TCP, UDP or HTTP).
Step 3:Now click on big button “IMMA CHARGIN MAH LAZER.” and start the attack.
Now see the bottom of the tool where you will find 5 fields under Attack status. When you will start attack, you will see that the number in Requested fields are increasing rapidly. This number show how many requestes have been send to website server.
But the important field is "Faild." If you see the increment in this field, it means attack has been working fine. It shows that server has stopped responding to the request. In other way, you can say that server is down. :P
Windows version of LOIC has a feature called HIVEMIND. This feature allows users to connect other systems on IRC server. In this way, attacker can collect more people in this attack and make it distributed over the internet.
To run this tool in HIVEMIND mode run this tool with command prompt with this command.
LOIC.exe /hivemind irc.server.address
After running the above command, your LOIC client will connect to irc://irc.server.adress:6667/loic
To run this tool in hidden mode, use this command
LOIC.exe /hidden /hivemind irc.server.address
In hidden mode, it will run without any visible GUI.
There are many DOS attacking tools are available which can be found here.
Dos Attacking Tools
But LOIC (Low Orbit Ion Cannon) is the best tool for DDOS attack and it is also used by most popular hacker group annonymous. There are two versions of this tool. One is the original binary version of the tool and other is the web based version called JS LOIC.
The best thing about this tool is that the tool does not require any kind of technical knowledge. It is so simple iin use. Just specify the the website and click on the attack button.
How To Use This Tool And Perform DOS Attack On A Website:
This tool is available for free. Download it from Sourceforge.Step 1: Run the tool. You will see the simple interface.
Step 2: At the top of the tool, there are two options. One for URL and other for IP. You can use any one. Enter the URL of the website which you want to take down. Now click on Lock On button. After that you are ready to attack on the website. Then, select attack method (TCP, UDP or HTTP).
Step 3:Now click on big button “IMMA CHARGIN MAH LAZER.” and start the attack.
Now see the bottom of the tool where you will find 5 fields under Attack status. When you will start attack, you will see that the number in Requested fields are increasing rapidly. This number show how many requestes have been send to website server.
But the important field is "Faild." If you see the increment in this field, it means attack has been working fine. It shows that server has stopped responding to the request. In other way, you can say that server is down. :P
How to Use LOIC and Perform DDOS attack
To run this tool in HIVEMIND mode run this tool with command prompt with this command.
LOIC.exe /hivemind irc.server.address
After running the above command, your LOIC client will connect to irc://irc.server.adress:6667/loic
To run this tool in hidden mode, use this command
LOIC.exe /hidden /hivemind irc.server.address
In hidden mode, it will run without any visible GUI.
MAKE UR PC FASTER
To MAKE UR PC FASTER than before,folow the steps
# Go to start then click run and then type REGDIT
# Select HKEY_CURRENT_USER and then select control panel folder and then select desktop folder. Do it correctly
# You will see registrysetting at your right hand side, after that select menu show delay and then right click and select modify .
# you will find edit string option -----> default value data is 400 , you have to change the value Datato 000
# Restart your computer. You will notice that your computer has becomemuch more faster.
(Note : This will help you to start your COMPUTER START quickly, to increase the overall performance please follow my another hub Make your COMPUTER FASTER and cleaner
# Go to start then click run and then type REGDIT
# Select HKEY_CURRENT_USER and then select control panel folder and then select desktop folder. Do it correctly
# You will see registrysetting at your right hand side, after that select menu show delay and then right click and select modify .
# you will find edit string option -----> default value data is 400 , you have to change the value Datato 000
# Restart your computer. You will notice that your computer has becomemuch more faster.
(Note : This will help you to start your COMPUTER START quickly, to increase the overall performance please follow my another hub Make your COMPUTER FASTER and cleaner
Subscribe to:
Comments (Atom)